Introduction
When testing Android applications, it is recommended to use a rooted device to perform the assessment efficiently and thoroughly. However, some applications have an additional layer of protection, which prevents an application from running on a rooted device. When presented with this scenario, one of the restrictions a tester need to overcome is the root-detection mechanism used by the application.
Several tools already exist to defeat an application’s root-detection mechanisms. But which one performs best? To answer this question, I decided to perform a comparison between these root-detection bypass tools. The goal of this experiment is to identify which tool performs best and to help analysts to have a “go-to” tool when bypassing an app’s root-detection implementation.
The target application used here is RootBeer Sample (v0.8); a sample app which utilizes the RootBeer library.
What is RootBeer?
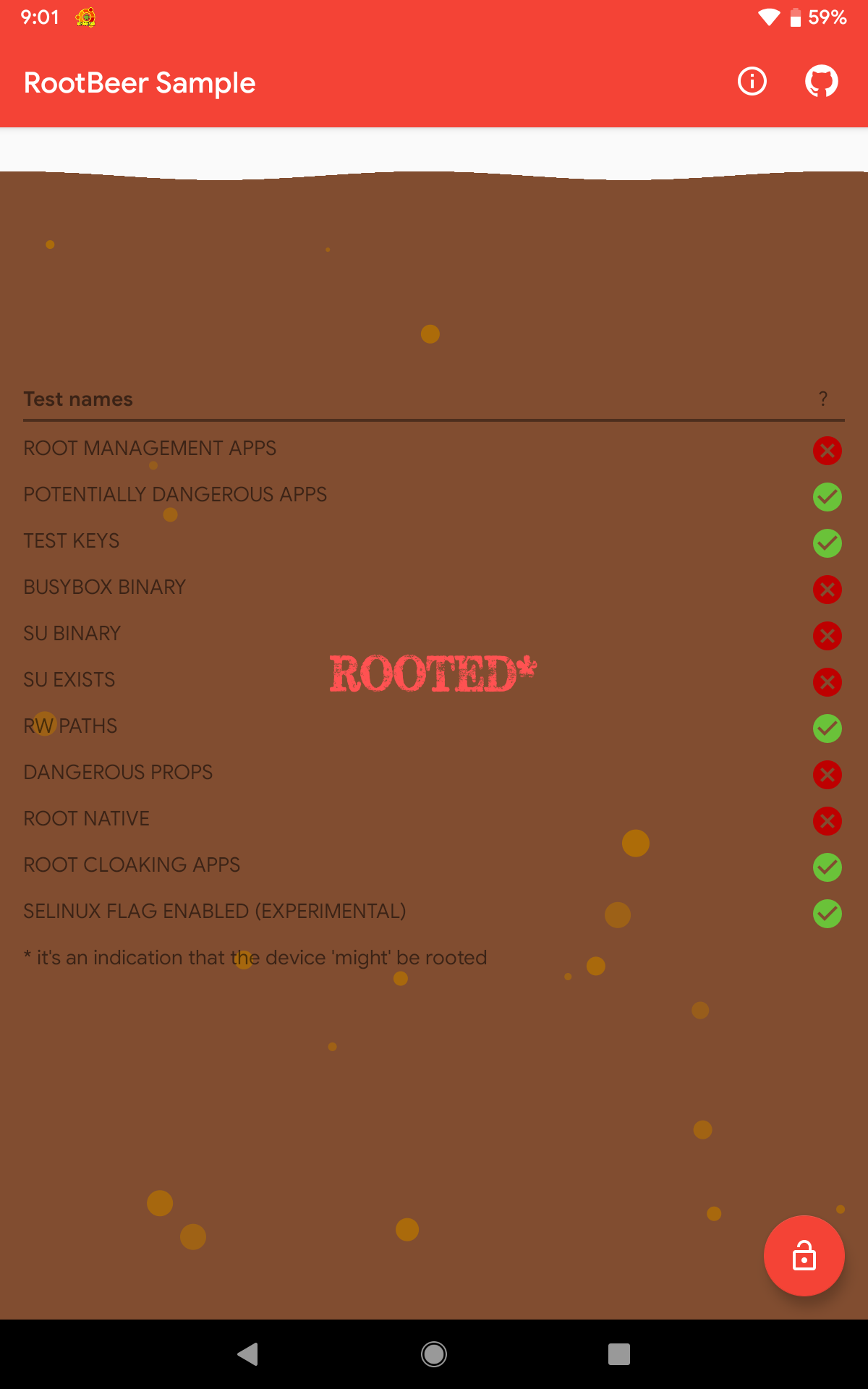
RootBeer is an open-source library which can be used by developers to verify the integrity of an Android device and check whether it is rooted or not. RootBeer performs the following checks as an indication of root:
- Presence of apps used to manage superuser/root access (e.g.,
eu.chainfire.supersuandcom.topjohnwu.magisk) - Installation of apps that require root (e.g.,
com.keramidas.TitaniumBackupandcom.chelpus.luckypatcher) - Detection of root-cloaking apps which can hide the root status of a device (e.g,
com.devadvance.rootcloak2) - Review of the build properties (
android.os.Build.TAGS) for test-keys - Locations of binaries, such as
busyboxandsu, which are usually present in a rooted device (e.g.,/system/xbin/"and/su/bin/) - Analysis of system folders that should not be writable (e.g.,
/system) - Look up of system properties that can only be changed when the device is rooted (e.g.,
ro.debuggableandro.secure)
Test Setup
The following Android device was used for this experiment:
- Device: Lenovo P8 (TB-8703F)
- Android Version: Pie (9.0)
- ROM: PixelExperience
This device was installed with the following applications which use and require root permissions:
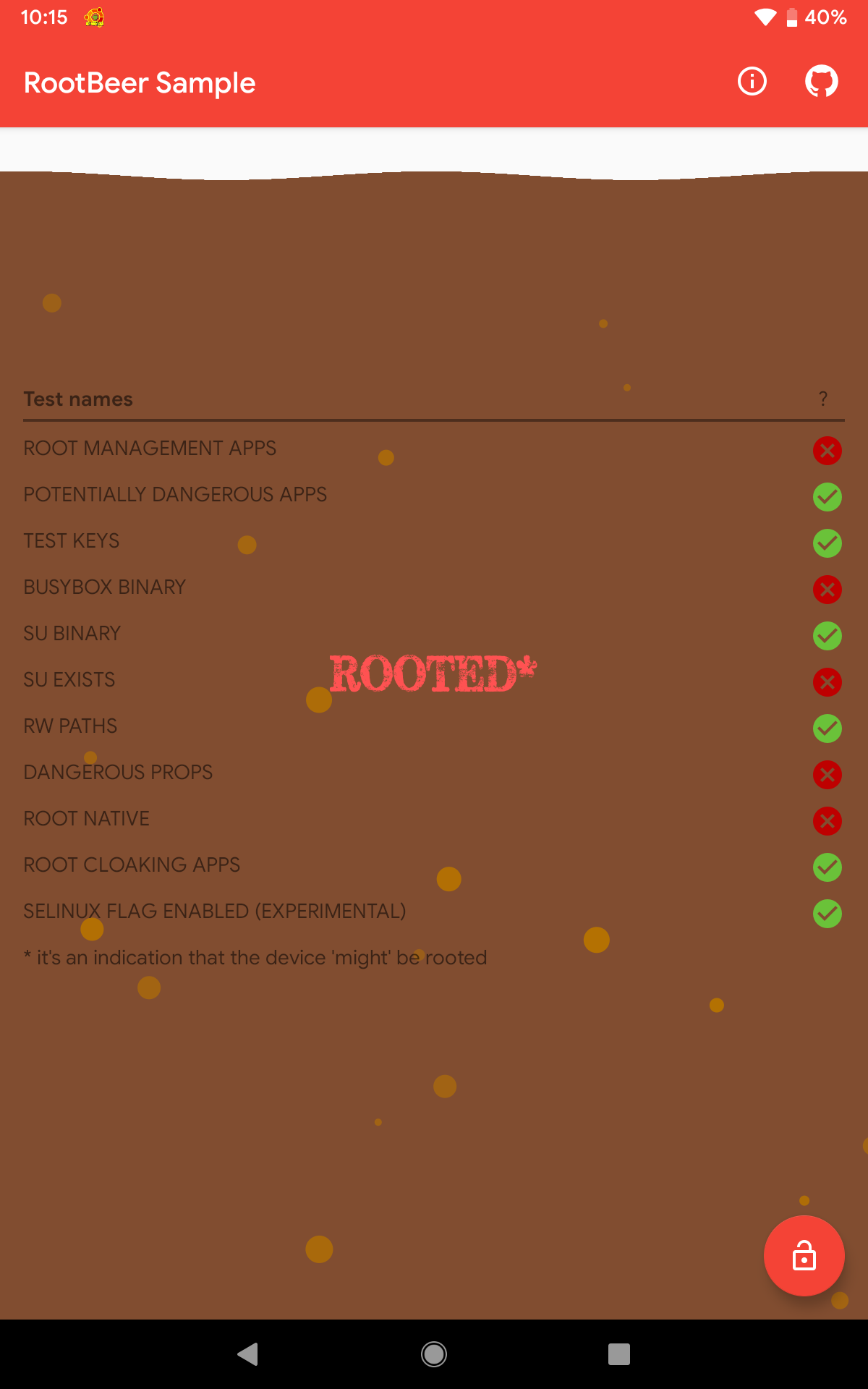
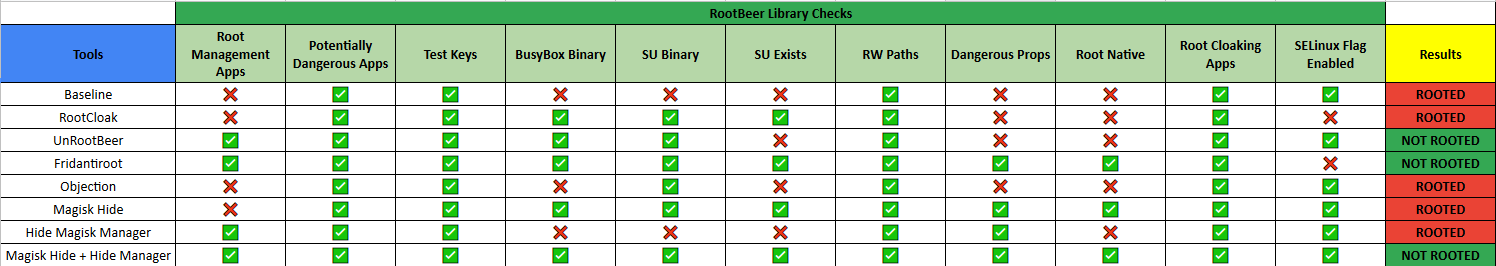
As a baseline for this experiment, RootBeer Sample was executed without any root-detection bypass tool used. Using this baseline setup, 6/11 checks failed.
List of Tools
This experiment only covered the following well-known and open-source root-detection bypass tools:
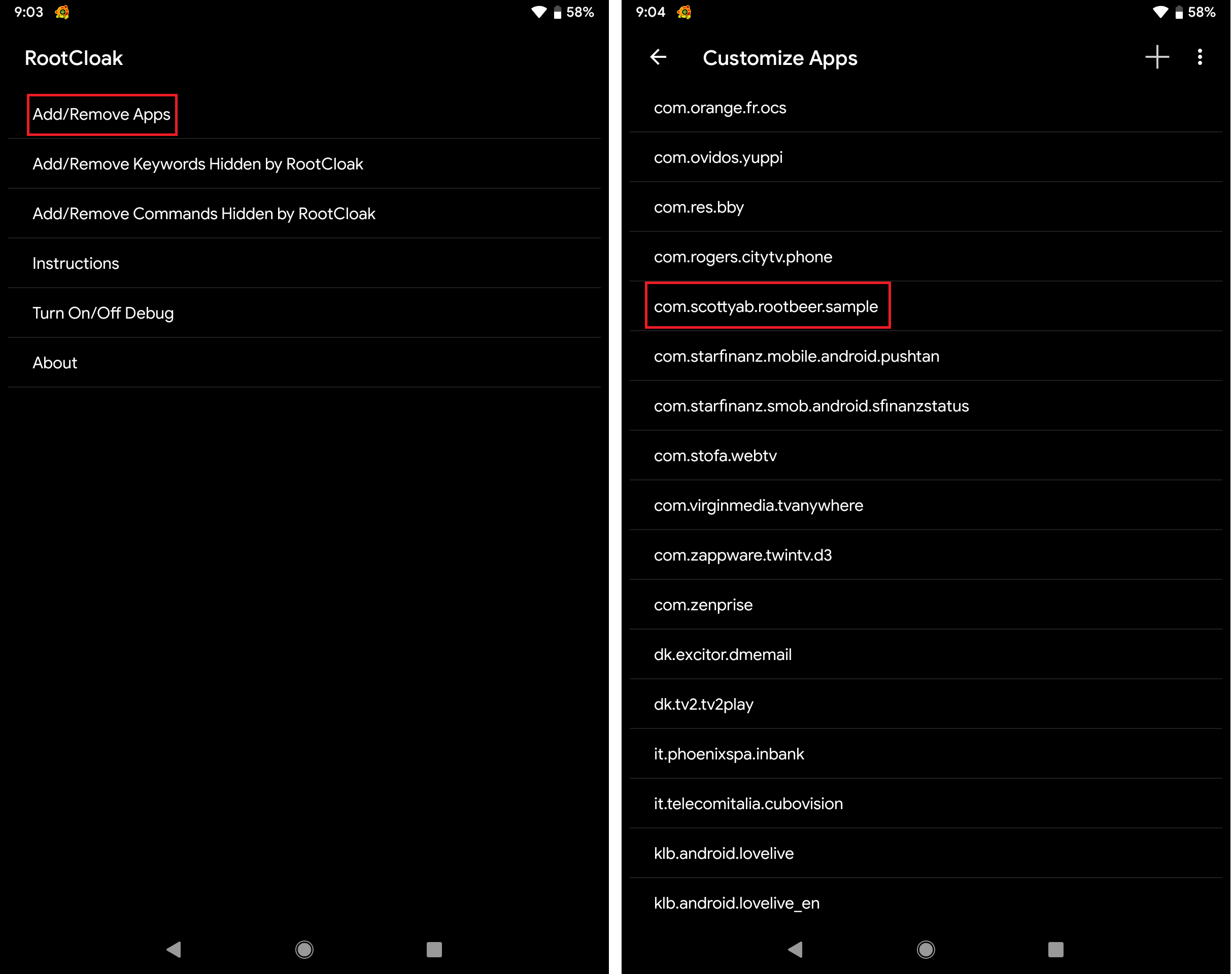
Tool #1: RootCloak
RootCloak is a very popular Xposed module that can be used to hide the root status of a device. Even though the module’s repo page states “with 5.x and 6.x support” and my device was running Android 9.0, I still tried it.
RootCloak is very simple to use. Just add the target application (RootBeer Sample in this case) and you’re good to go.
Surprisingly, RootCloak bypassed some checks used by RootBeer library. Even though there’s no official statement that the module supports Android 9.0, it still worked. Using RootCloak, 7/11 checks were bypassed.
Tool #2: UnRootBeer
The next tool is UnRootBeer, which is another Xposed module specifically developed to disable the checks performed by RootBeer library. To use this tool, just install the APK file, and reboot the device to activate the module.
As seen from the result below, UnRootBeer performed better than RootCloak as it passed 8/11 checks. While this tool was specifically developed to bypass the checks being performed by RootBeer library, it is not surprising that it failed some checks because this tool has not been updated for quite some time.
Be wary though because while three checks failed, the result still says NOT ROOTED. The goal of this experiment is to pass all RootBeer library checks.
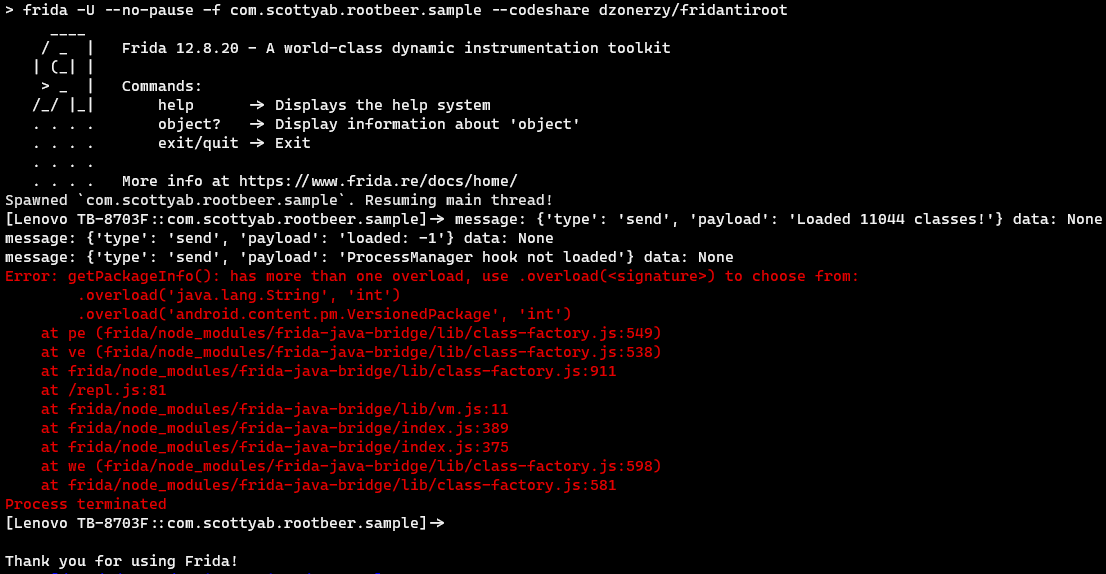
Tool #3: Fridantiroot
The next tool involves Frida, which is a dynamic instrumentation toolkit that can be used to tamper an application’s process. For this experiment, the publicly available JS script (Fridantiroot) was used. However, this script didn’t work on my device (at the time of doing this experiment).
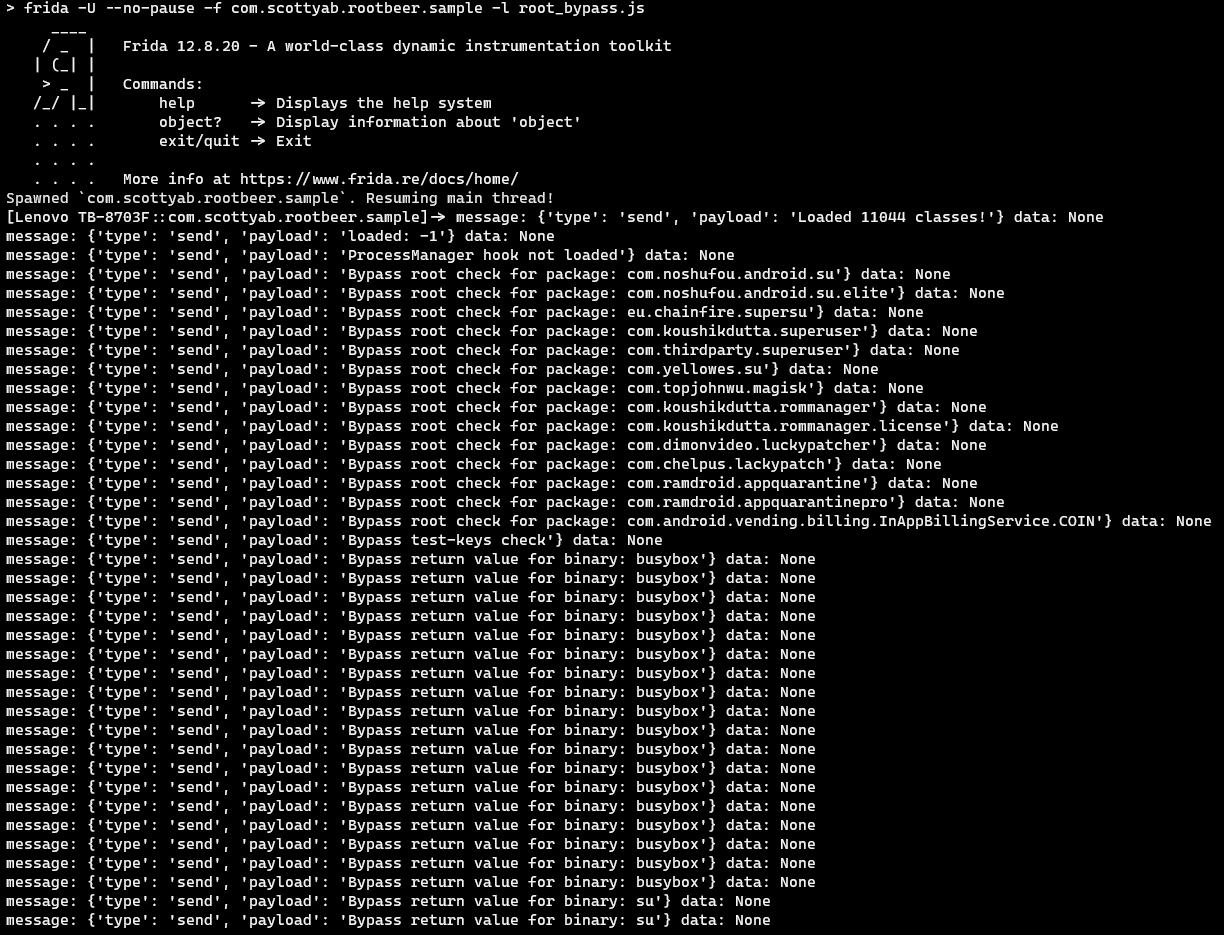
Luckily, I found a modified version of Fridantiroot which worked on my device.
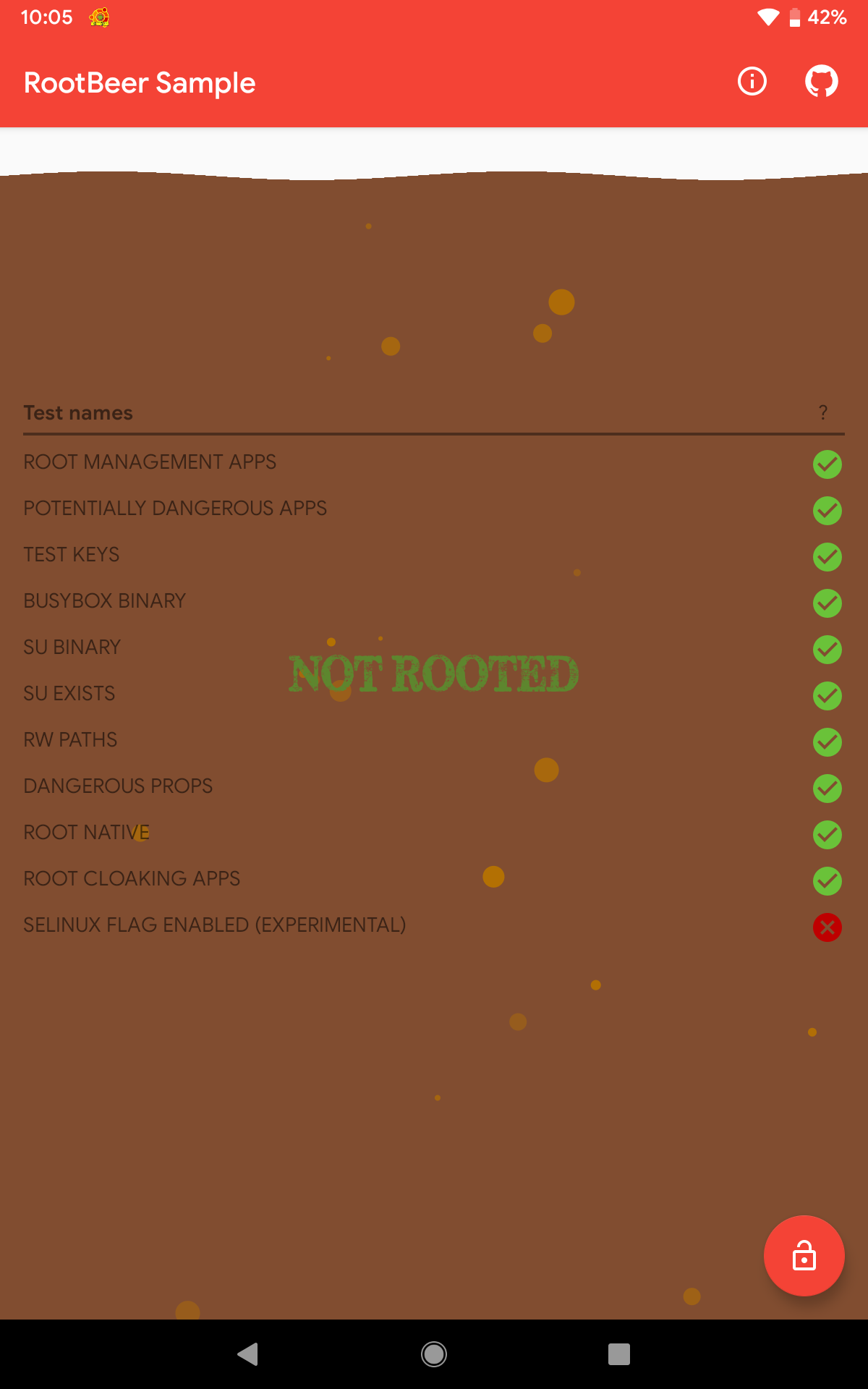
The result was very surprising because it almost passed all the checks, with a score of 10/11.
Please note that one of the checks failed and yet the app still considered it as NOT ROOTED.
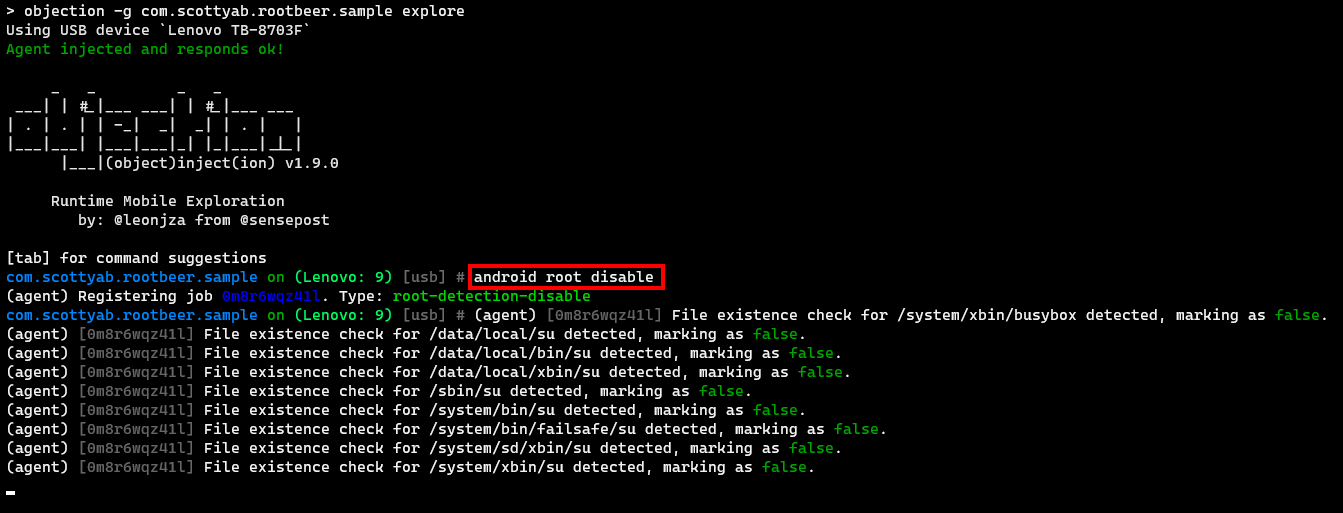
Tool #4: Objection
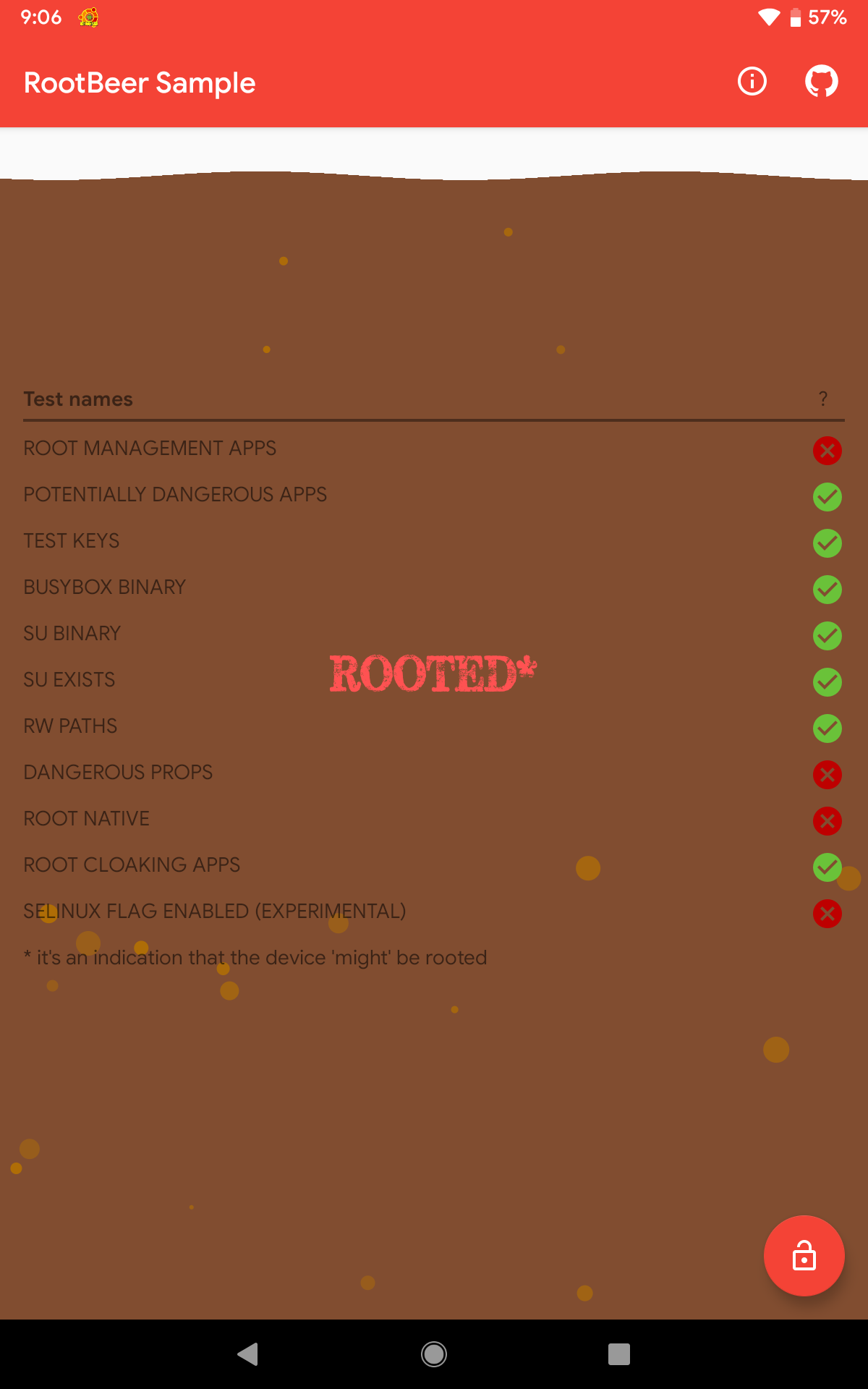
Objection is a runtime toolkit powered by Frida. Using the command android root disable, objection will attempt to bypass an app’s root-detection mechanism.
As seen below, objection’s root-detection bypass command didn’t provide a pleasing result, as it only passed 5 out of 11 checks.
Tool #5: Magisk Hide
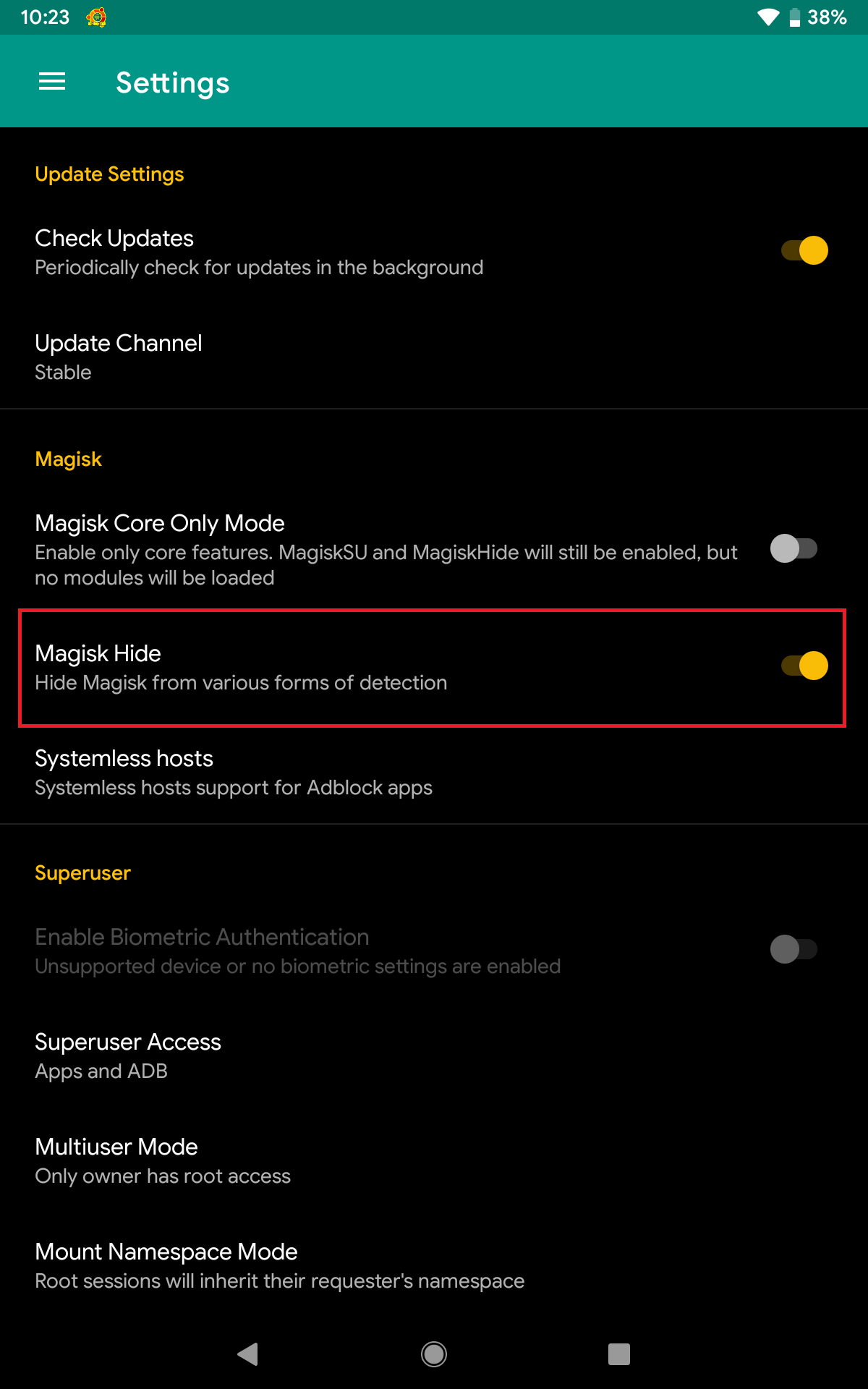
One of the features of Magisk is Magisk Hide, which can be used to bypass root-detection and system integrity checks.
Since Magisk v20.4, Magisk Hide is disabled by default. To enable this feature, open Magisk Manager, click Settings from the sidebar, toggle ON the Magisk Hide option, and restart the app.
Take note that Magisk Hide and Frida do not work well together. To use one of them, the other one must be disabled first.
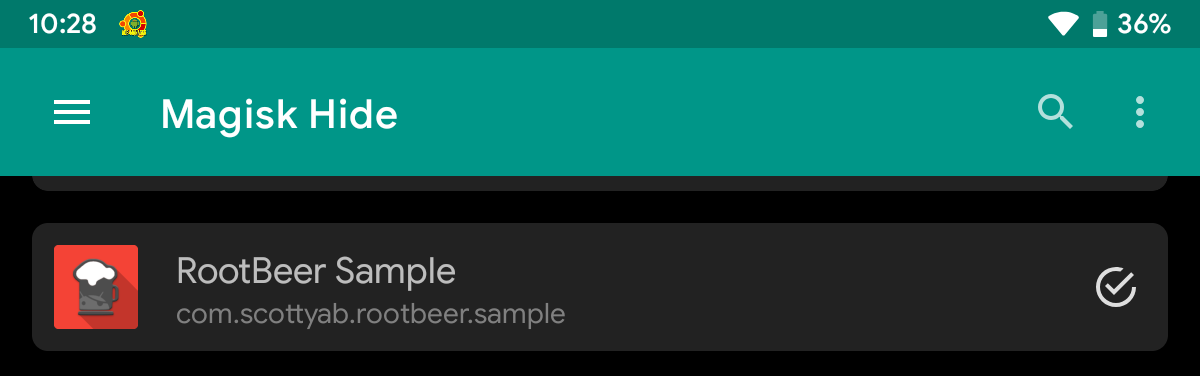
Bypassing an app’s root-detection mechanism is as simple as adding the app to the Hide list (just like in RootCloak).
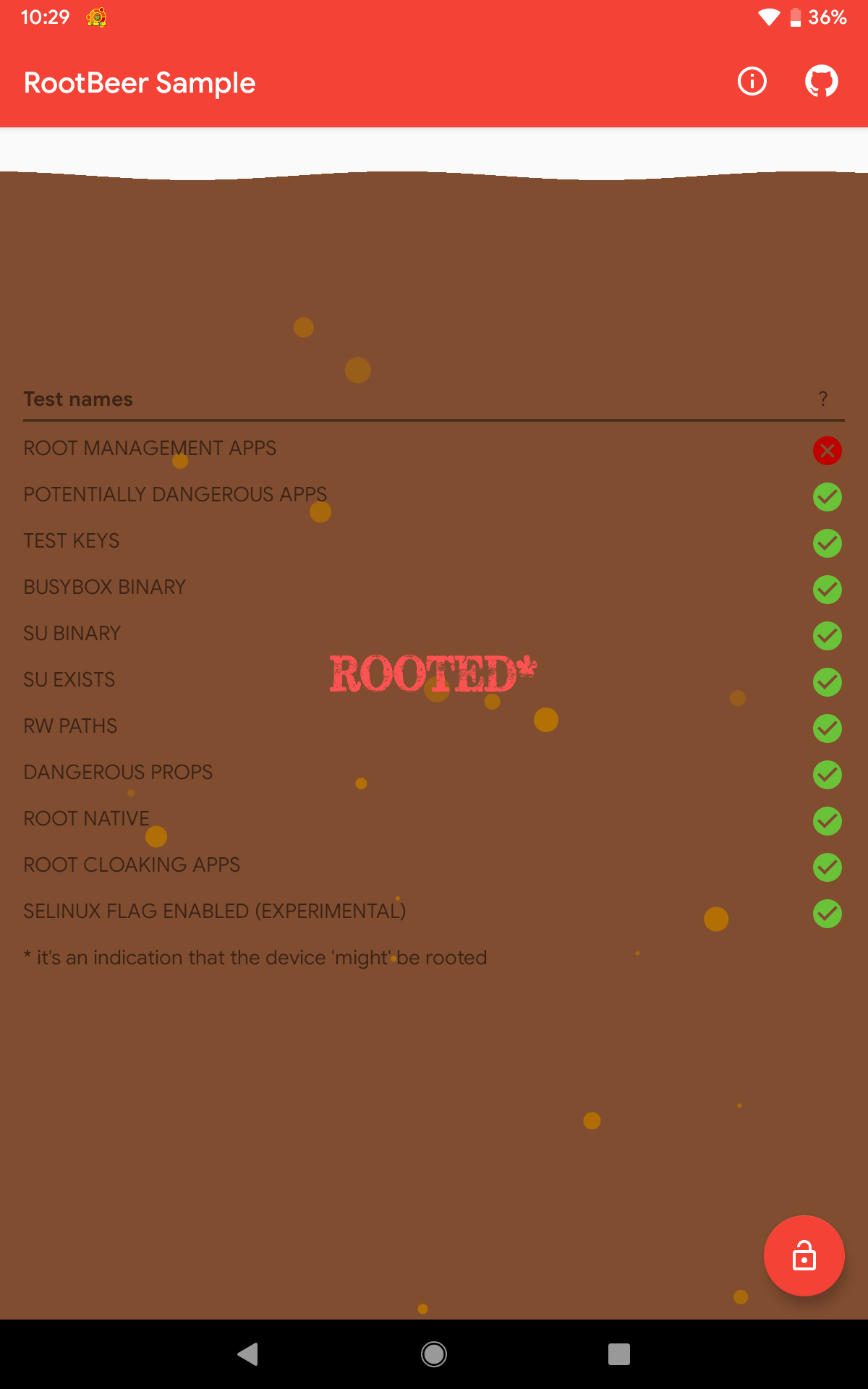
After adding RootBeer Sample to Magisk Hide, the result was a near-perfect score, with 10 out of 11 checks were passed.
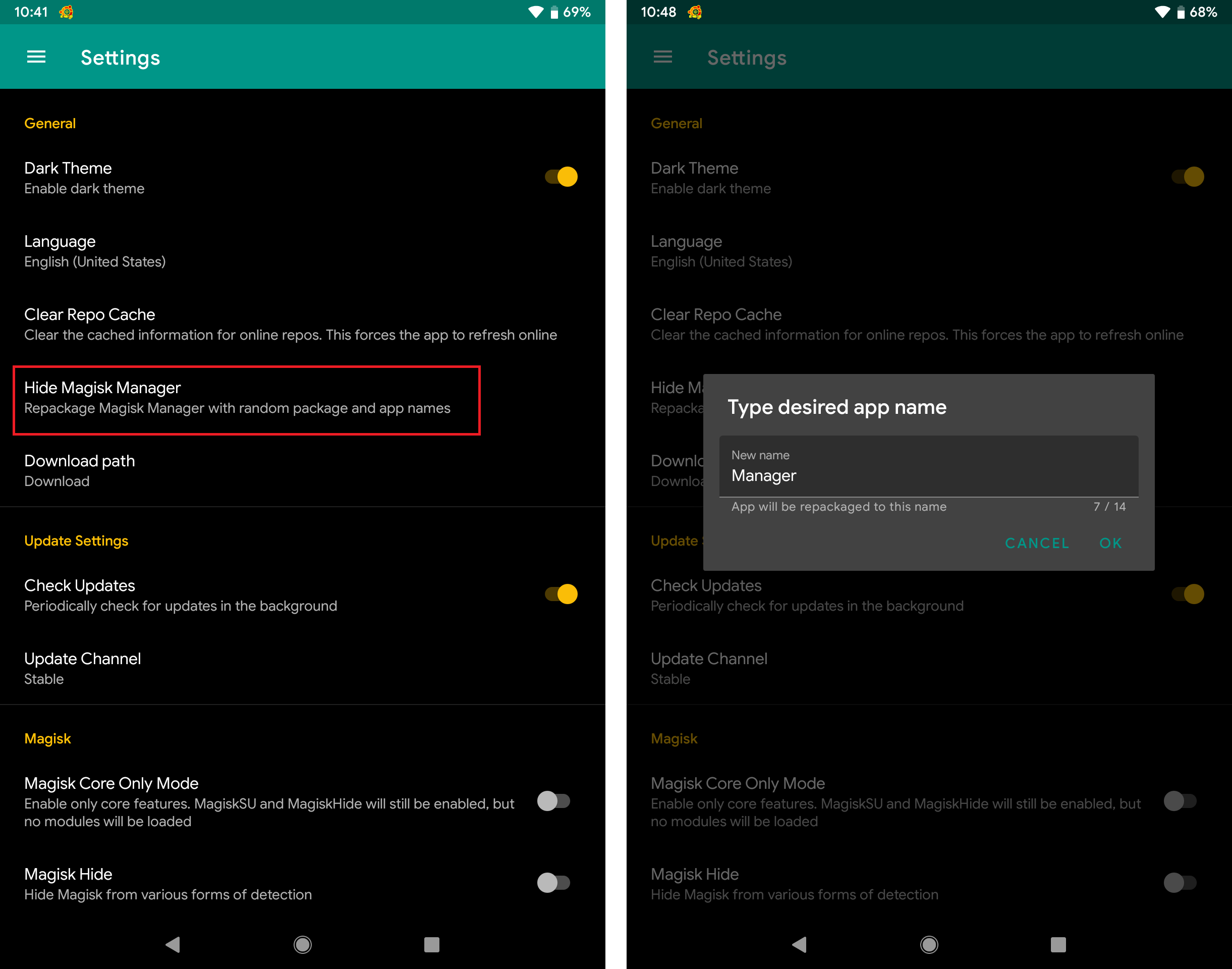
Tool #5: Hiding Magisk Manager
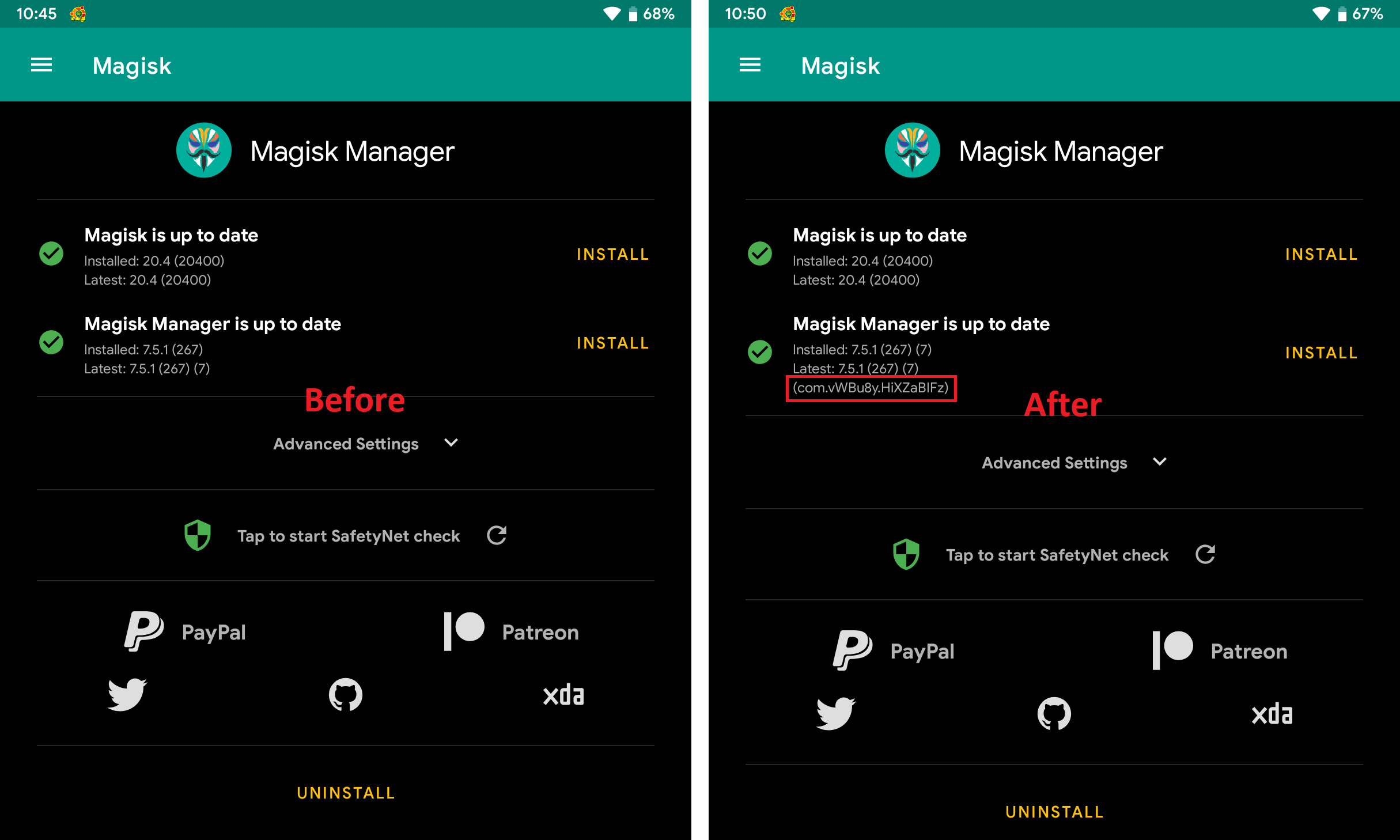
Looking back at the result of using Magisk Hide, only the first check (Root Management Apps) failed. This was because one of the checks used by RootBeer library is to look for the presence of root management apps, such as Magisk Manager (com.topjohnwu.magisk).
Since Magisk v20.1, a new feature was introduced that could repackage Magisk Manager with a random package and app names. To use this feature, click the Settings option from the sidebar, click the Hide Magisk Manager option, and set Magisk Manager’s new app name.
After doing the above steps and using this feature, Magisk Manager’s package name changed to a random one.
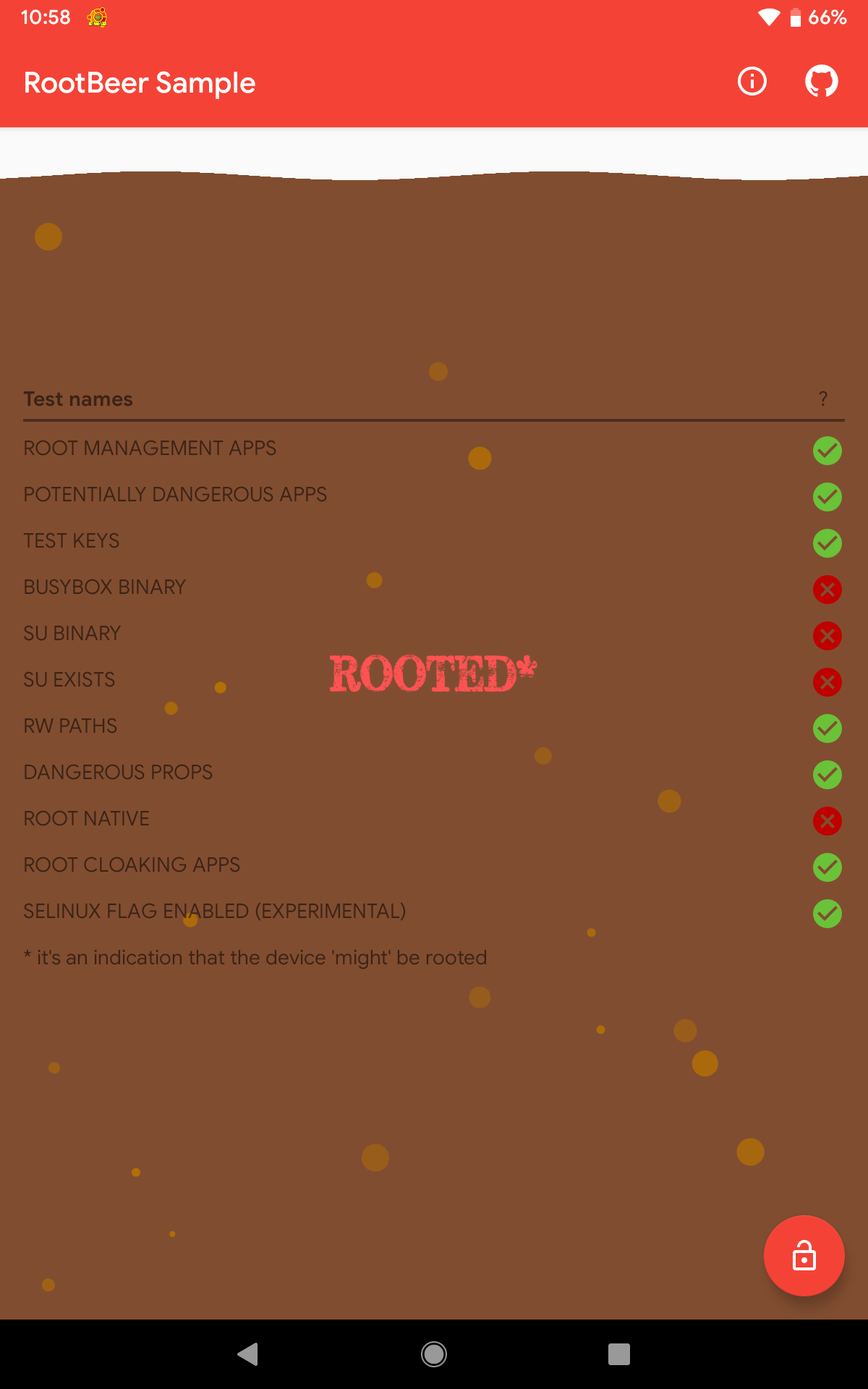
So how did it perform? Well, it did not do well and only 7 checks passed.
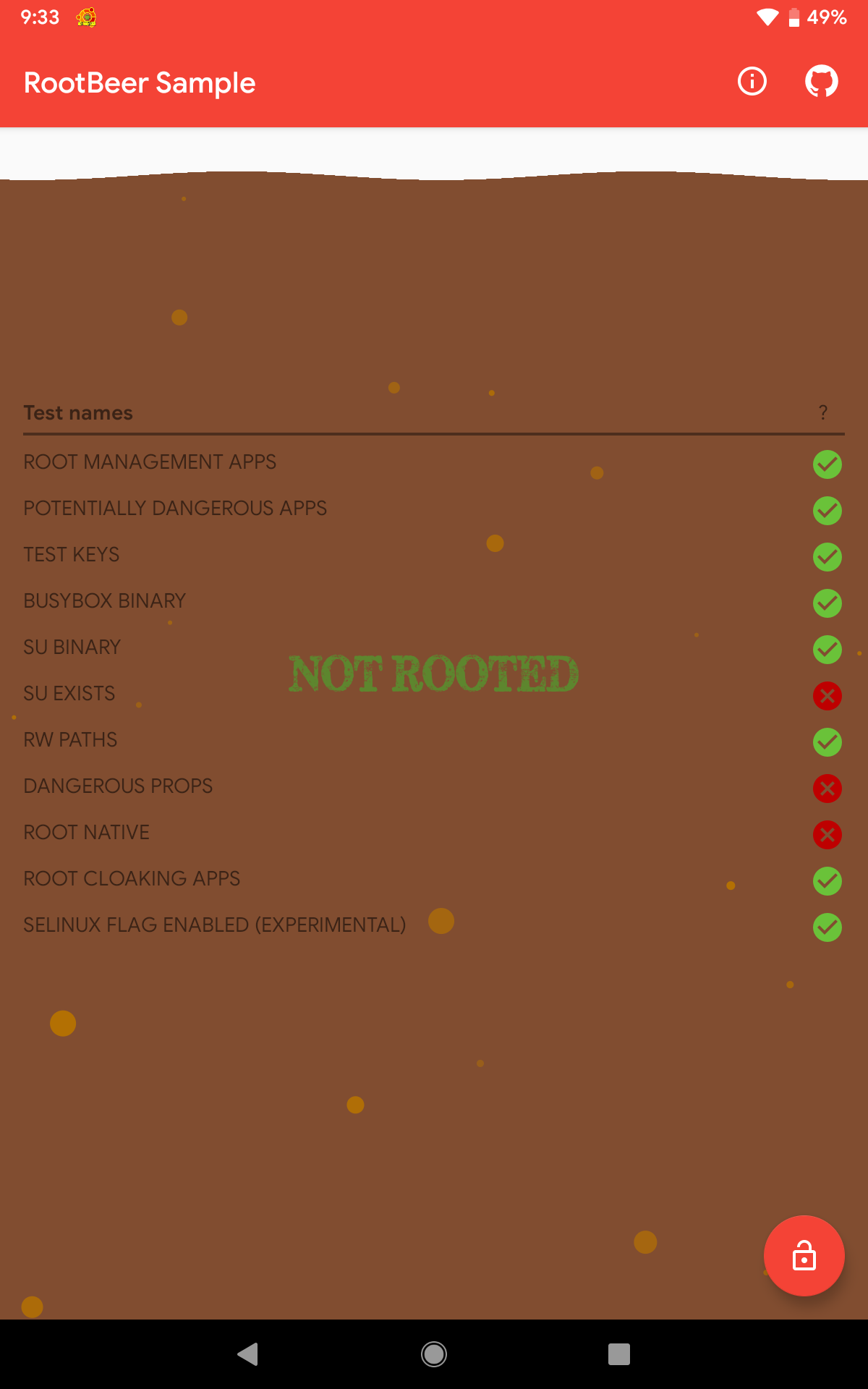
Tool #5: Magisk Hide + Hiding Magisk Manager
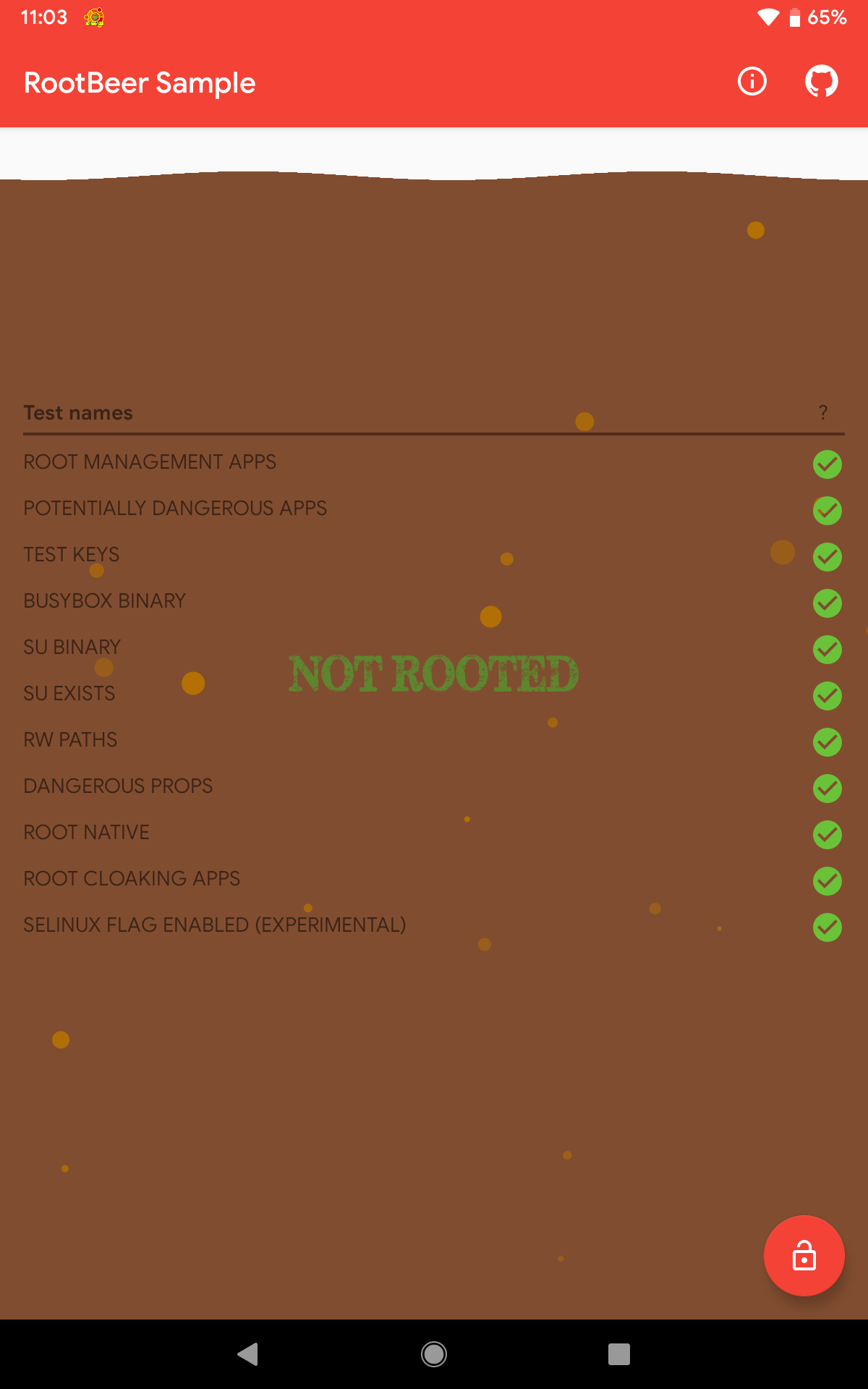
Since Magisk Hide and Hide Magisk Manager are both features of Magisk, why not use both features at the same time? It turned out that this was what we’re aiming for. The result was outstanding! The result stating that it is NOT ROOTED was valid since all checks passed.
Results
For ease of viewing, the following table summarizes the results obtained from this experiment.
Among all the tools covered in this experiment, only Magisk’s features (Magisk Hide and Hiding Magisk Manager) gave the best result.
Final Thoughts
While the goal of this experiment is to have a “go-to” tool when bypassing root-detection mechanisms, testers should be aware that the results gathered here will not always be the same against every application. This is because app developers can modify and improve the RootBeer library by adding more checks, or they could use their custom anti-root solutions. Thus, I encourage analysts to also learn how to reverse engineer an application and bypass an app’s root-detection manually.
Lastly, no root-detection mechanism can ever be perfect. That’s why it is recommended to implement additional security measures to make a bypass more difficult to achieve. Such measures include the use of run-time protections, as well as anti-reversing and anti-tampering solutions.